Contents of “Embedded Software for the IoT”
Table of contents (third edition) for the IoT-book is shown with a few selected figures. Read more about the book here.
1 Introduction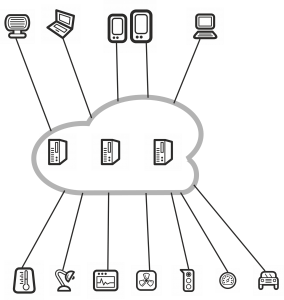
1.1 The Tale of the Internet
1.2 The Cloud
1.3 Internet of Things
1.4 IoT Related Terms
I The Basic System
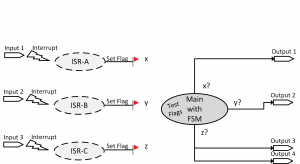 2 How to select an OS?
2 How to select an OS?
2.1 No OS and Strictly Polling
2.2 Co-routines
2.3 Interrupts
2.4 A Small Real-time Kernel
2.5 A non-preemptive Operating System
2.6 Full OS
2.7 Open Source, GNU licensing and Linux
2.8 OS constructs
2.9 Further Reading
 3 Which CPU to use?
3 Which CPU to use?
3.1 Overview
3.2 CPU Core
3.3 CPU Architecture
3.4 Word-Size
3.5 MMU – Memory Managed Unit
3.6 RAM
3.7 Cache
3.8 EEPROM and Flash
3.9 FPU – Floating Point Unit
3.10 DSP
3.11 Crypto-Engine
3.12 Upgrade Path
3.13 Second Sources
3.14 Price
 3.15 Export Control
3.15 Export Control
3.16 RoHS-Compliance
3.17 Evaluation Boards
3.18 Tool-chain
3.19 Benchmarking
3.20 Power Consumption
3.21 JTAG Debugger
3.22 Peripherals
3.23 Make or Buy
3.24 Further Reading
4 Software Architecture
 4.1 Design for Performance
4.1 Design for Performance
4.2 The fear of the white paper
4.3 Layers
4.4 Not just API’s – More Files
4.5 Object Model (Containment Hierarchy)
4.6 Case: CANOpen
4.7 Message Passing
4.8 Middleware
4.9 Case: Architectural Reuse in LAN-XI
4.10 Understanding C
4.11 Further Reading
5 Debug Tools
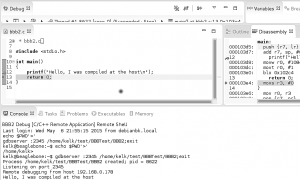 5.1 Simulator
5.1 Simulator
5.2 ICE – In-Circuit-Emulator
5.3 Background or JTAG debugger
5.4 Target Stand-In
5.5 Debugger
5.6 strace
5.7 Debugging Without Special Tools
5.8 Monitoring Messages
5.9 Test Traffic
6 Code Maintenance
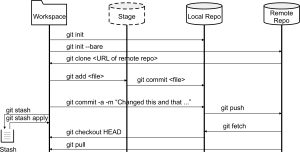 6.1 Poor Mans Backup
6.1 Poor Mans Backup
6.2 Version Control – and git
6.2.1 Github and other Cloud Solutions
6.3 Build and Virtualization
6.4 Static Code Analysis
6.5 Inspections
6.6 Tracking Defects & Features
6.7 Whiteboard
6.8 Documentation
6.9 Yocto
6.10 OpenWRT
6.11 Further Reading
III IoT Technologies
7 Networks (see free download of this chapter here)
7.1 Introduction to the Internet Protocols
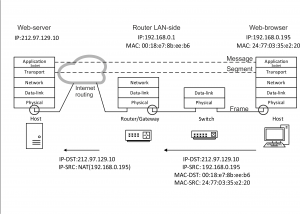
7.2 Cerf & Kahn – Internet as Net of Nets
7.3 Life of a Packet
7.4 Life Before the Packet
7.5 Getting an IP address
7.6 DHCP
7.7 Network Masks, CIDR and Special Ranges
7.8 Reserved IP Ranges
7.9 DNS
7.10 Introducing HTTP
7.11 REST
7.12 TCP sockets on IPv4 under Windows
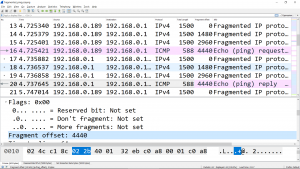 7.13 IP Fragmentation
7.13 IP Fragmentation
7.14 Introducing IPv6 addresses
7.15 TCP sockets on IPv6 under Linux
7.16 Data Transmission
7.17 UDP Sockets
7.18 Case: UDP on IPv6
7.19 Application Layer Protocols
7.20 Alternatives to the socket API
7.21 Ethernet Cabling
7.22 Physical Layer Problems
7.23 Further Reading
8 Network Tools
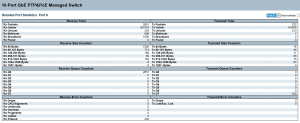
8.1 Finding the IP Address
8.2 The Switch as a Tool
8.2.1 Mirroring
8.2.2 Statistics
8.2.3 Simulating lost frames
8.2.4 Pause frames
8.3 Tap
8.4 SNMP
8.5 Wireshark
8.6 Network Commands
8.8 Further Reading
9 Wireless Networks
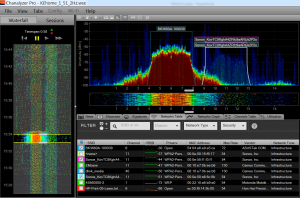 9.1 Introduction
9.1 Introduction
9.2 WiFi Basics
9.3 The Access Point as a Repeater
9.4 How is speed calculated?
9.5 Case: WiFi Data-transmission
9.6 Case: Beacons
9.7 Case: A strange lagging
9.8 Aggregated Frames
9.9 Channel Assessment
9.10 Bluetooth Low Energy
9.11 Certification
9.12 Further Reading
10 Security
 10.1 Introduction
10.1 Introduction
10.2 The goals of a Hacker
10.3 Network Security Concepts
10.4 Hash-function
10.5 Symmetric Key Encryption
10.6 Case: Enigma
10.7 Asymmetric Key Encryption
10.8 Digital Signature
10.9 Certificates
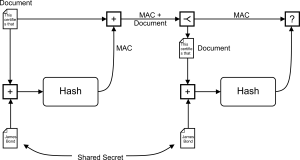
10.10 Message Authentication Code
10.11 Nonce
 10.12 Secure Socket Communication
10.12 Secure Socket Communication
10.13 OpenSSL
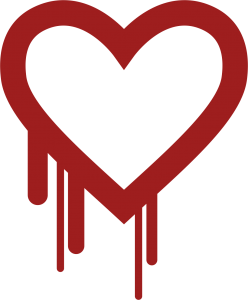
10.14 Case: Heartbleed
10.15 Case: WiFi Security
10.16 Software Crypto Libraries
10.17 Trusted Platform Module
10.18 Embedded Systems
10.19 Vulnerabilities in Embedded Systems
10.20 Export Control
10.21 Further Reading
11 Digital Filters
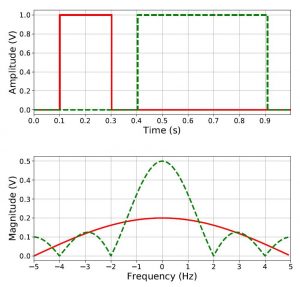
11.1 Why Digital?
11.2 Why Filters?
11.3 About the Sampling Frequency
11.4 Time and Frequency Domains
11.5 Analog and Digital Definitions
11.6 More Duality
11.7 A Well-behaving System
11.8 IIR filter Basics
11.9 Implementing IIR
11.10 FIR Filter basics
11.11 Implementing FIR
11.8 Integers
11.12 Dynamic Range versus Precision
11.13 Integers
11.14 Fixed Point Arithmetic
11.10 Q-Notation and Multiplication
11.11 Division
11.12 BCD
11.13 Further Reading
12 Statistical Process Control
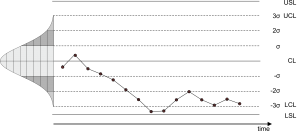 12.1 Introduction
12.1 Introduction
12.2 Important terms
12.3 Control Charts
12.4 Finding the Control Limits
12.5 Subgroups
12.6 Case: Insulation Plates
12.7 EWMA Control Charts
12.8 Process Capability Index
12.9 Further Reading
Epilogue
